After spending considerable time exploring automation platforms and the challenges they face with Microsoft 365 integrations, we've developed a solution that addresses one of the most persistent pain points in the automation space: multi-user credential management.
MS Auto Auth 365, a self-hosted application that fundamentally changes how organisations approach automation workflows involving Microsoft services.
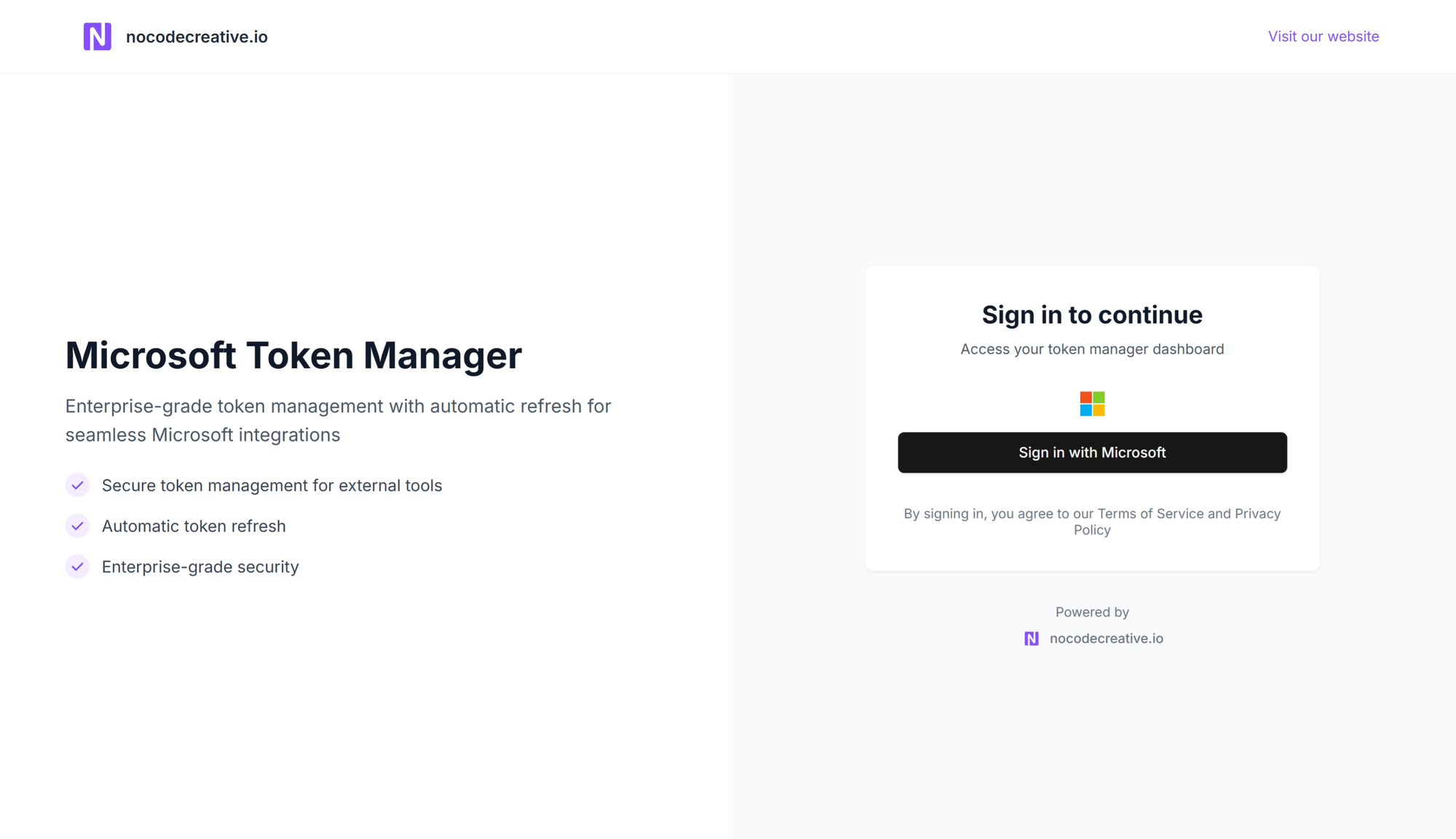
What the Application Does
At its core, this platform serves as a centralised authentication hub for Microsoft 365 services, designed specifically to solve the token management challenges that plague modern automation workflows.
The application handles OAuth token lifecycle management for multiple users across your organisation, providing a secure API that automation tools can leverage without requiring individual credential setup for each workflow. Rather than storing Microsoft credentials directly in tools like n8n, Make or Zapier, your automation workflows connect to this central platform to retrieve fresh, valid tokens as needed.
Here's what makes it particularly clever: the platform manages tokens for both Microsoft Graph API and SharePoint API access, with configurable scopes defined in the .env.example file:
# Microsoft Graph scopes
MS_GRAPH_SCOPES=openid,offline_access,profile,email,User.Read,Mail.Read,Mail.Send,Calendars.Read,Chat.ReadWrite,ChatMessage.Send,OnlineMeetings.Read,OnlineMeetingTranscript.Read.All,Chat.ReadWrite.All,Files.Read.All,Sites.Read.All
# SharePoint scopes
MS_SHAREPOINT_SCOPES=AllSites.Read,MyFiles.Read,Sites.Search.All,Sites.Selected,User.Read.All
The system automatically handles token refresh cycles, ensuring your automation workflows never fail due to expired credentials—a common frustration point I've encountered with direct OAuth integrations.
Intended Purpose
The problem this platform solves is both common and significant: enabling secure, scalable multi-user Microsoft 365 automation without the complexity of individual credential management.
Traditional automation setups face several critical limitations:
- Limited User Context: Automations typically run under a single service account, losing the ability to act on behalf of specific users
- Maintenance Overhead: Tokens expire, credentials change, and manual intervention becomes a constant requirement
- Security Risks: Storing individual user credentials across multiple automation platforms creates security vulnerabilities
- Scalability Issues: Adding new users or workflows becomes increasingly complex as your automation ecosystem grows
This platform transforms that paradigm entirely. As detailed in the README.md, it provides:
"A centralised, secure hub for managing OAuth tokens across your organisation. Users authenticate once through standard Microsoft OAuth flows, and automation tools access these tokens via a secure API."
The architecture creates a robust Express.js server that handles the complex OAuth flows while exposing a simple, secure API for your automation tools to consume.
Key Features
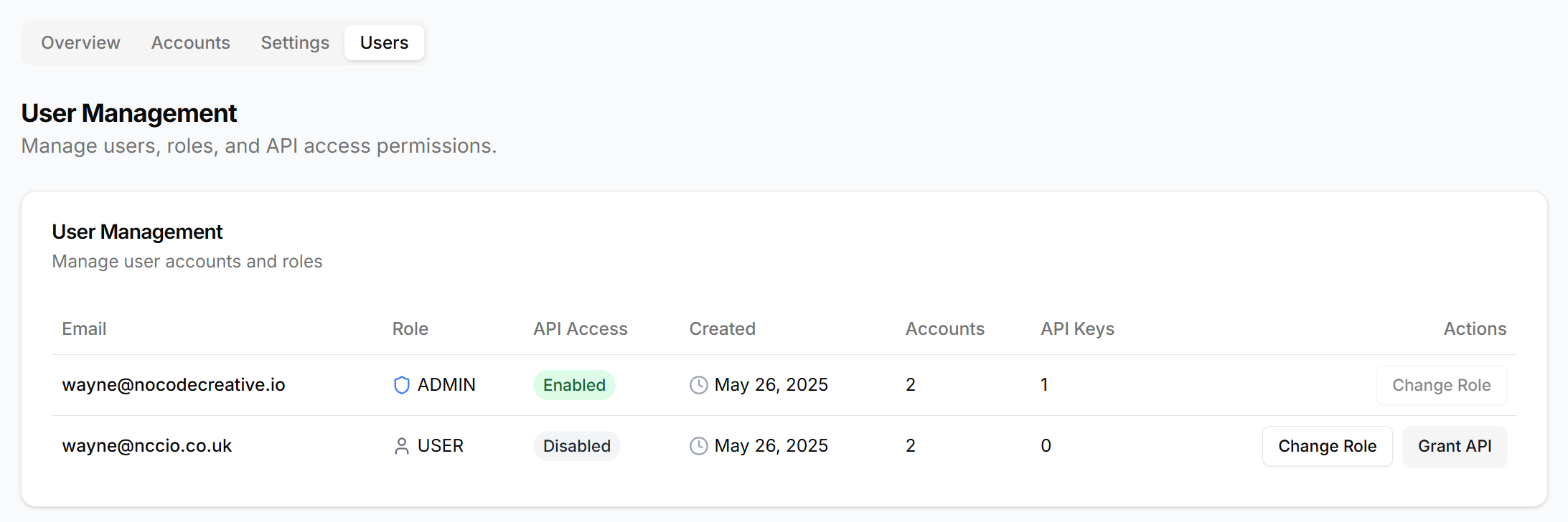
User Management & Role-Based Access Control
The system implements a sophisticated RBAC model supporting two primary roles:
- Admin Role: Full system access, user management capabilities, and unrestricted API access
- User Role: Access to personal tokens and controlled API permissions
The first user to authenticate automatically receives admin privileges.
API Access
When you purchase the platform, you're getting access to a production-ready REST API designed specifically for automation workflows. Here's what your tools can access:
Core Token Retrieval API
GET /api/external/tokens
This is the heart of the system, your automation tools call this endpoint to retrieve fresh, valid Microsoft tokens for any user in your organisation.
Key Features:
- Returns encrypted access tokens for all connected Microsoft accounts
- Role-based filtering (regular users see only their tokens, admins see everything)
- Automatic token refresh handling—you never get expired tokens
- Support for both Microsoft Graph and SharePoint APIs
Query Parameters:
# Filter by specific user (admin only)
?userId=user-123
# Filter by email address (admin only)
?email=john@company.com
# Get tokens for specific account
?accountId=account-456Example Response:
{
"accounts": [
{
"id": "account-id",
"userId": "user-id",
"provider": "microsoft",
"tenantId": "your-tenant",
"accessToken": {
"type": "Buffer",
"data": [/* encrypted token data */]
},
"refreshToken": {
"type": "Buffer",
"data": [/* encrypted refresh token */]
},
"expiresAt": "2024-01-01T00:00:00Z",
"scope": ["User.Read", "Mail.Send", "..."],
"status": "ACTIVE"
}
]
}The beauty of this approach; Your automation workflows never need to worry about token expiry, refresh cycles, or OAuth complexity. They just call this endpoint and get working tokens.
Token Decryption Integration
The platform returns encrypted tokens for security. If you self-host n8n, we recommend adding your token encryption key as an environment variable in your n8n stack. Here's how to integrate with n8n:
N8N Integration Example
To decrypt tokens, use the following code snippet in a code node:
const crypto = require('crypto');
// TOKEN_KEY (same as in your .env file)
const TOKEN_KEY = '<your-encryption-key>';
// Generate encryption key from TOKEN_KEY
const encryptionKey = crypto.createHash('sha256').update(TOKEN_KEY).digest();
// Store results
let results = [];
for (const item of items) {
const accounts = item.json.accounts || [];
for (const account of accounts) {
try {
// Ensure the accessToken and its data are defined
if (!account.accessToken?.data || !Array.isArray(account.accessToken.data)) continue;
// Create buffer from token data
const encryptedBuffer = Buffer.from(account.accessToken.data);
// Extract IV and encrypted content
const iv = encryptedBuffer.slice(0, 16);
const encryptedContent = encryptedBuffer.slice(16);
// Decrypt the token
const decipher = crypto.createDecipheriv('aes-256-cbc', encryptionKey, iv);
let decryptedToken = decipher.update(encryptedContent, null, 'utf8');
decryptedToken += decipher.final('utf8');
// Add to results
results.push({
json: {
accessToken: decryptedToken,
userId: account.userId,
provider: account.provider,
tenantId: account.tenantId,
}
});
} catch (error) {
// Optionally push error details for debugging
results.push({
json: {
error: `Failed to decrypt token for provider ${account.provider}`,
details: error.message
}
});
}
}
}
return results;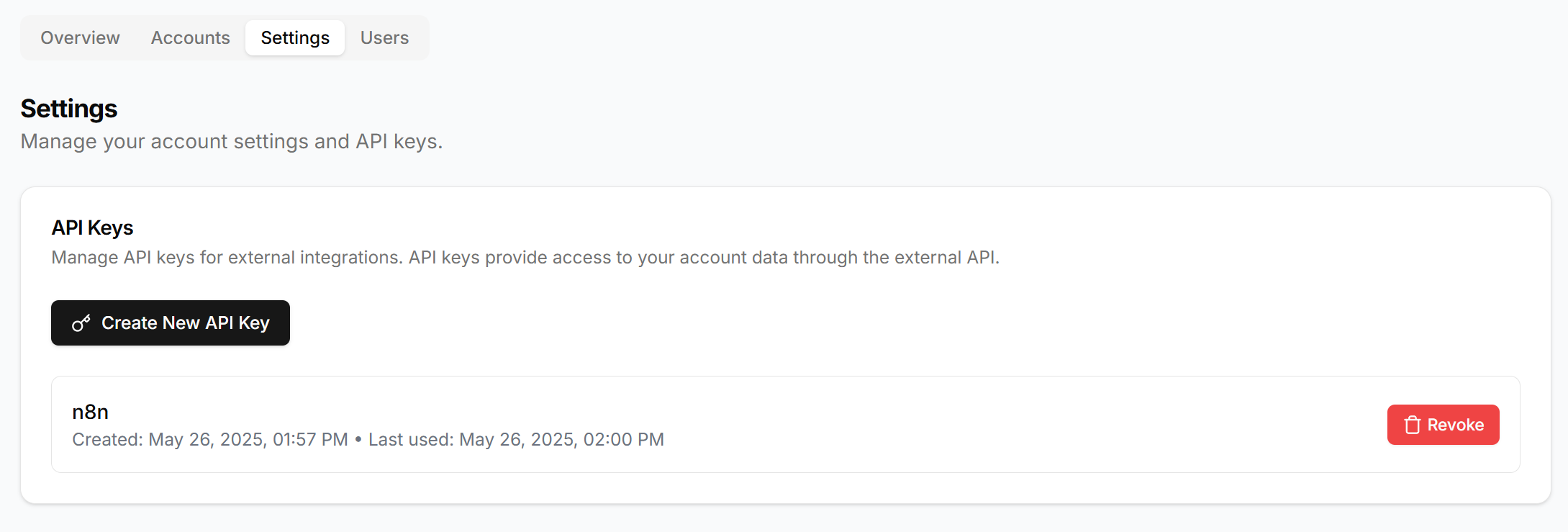
Token Lifecycle Management
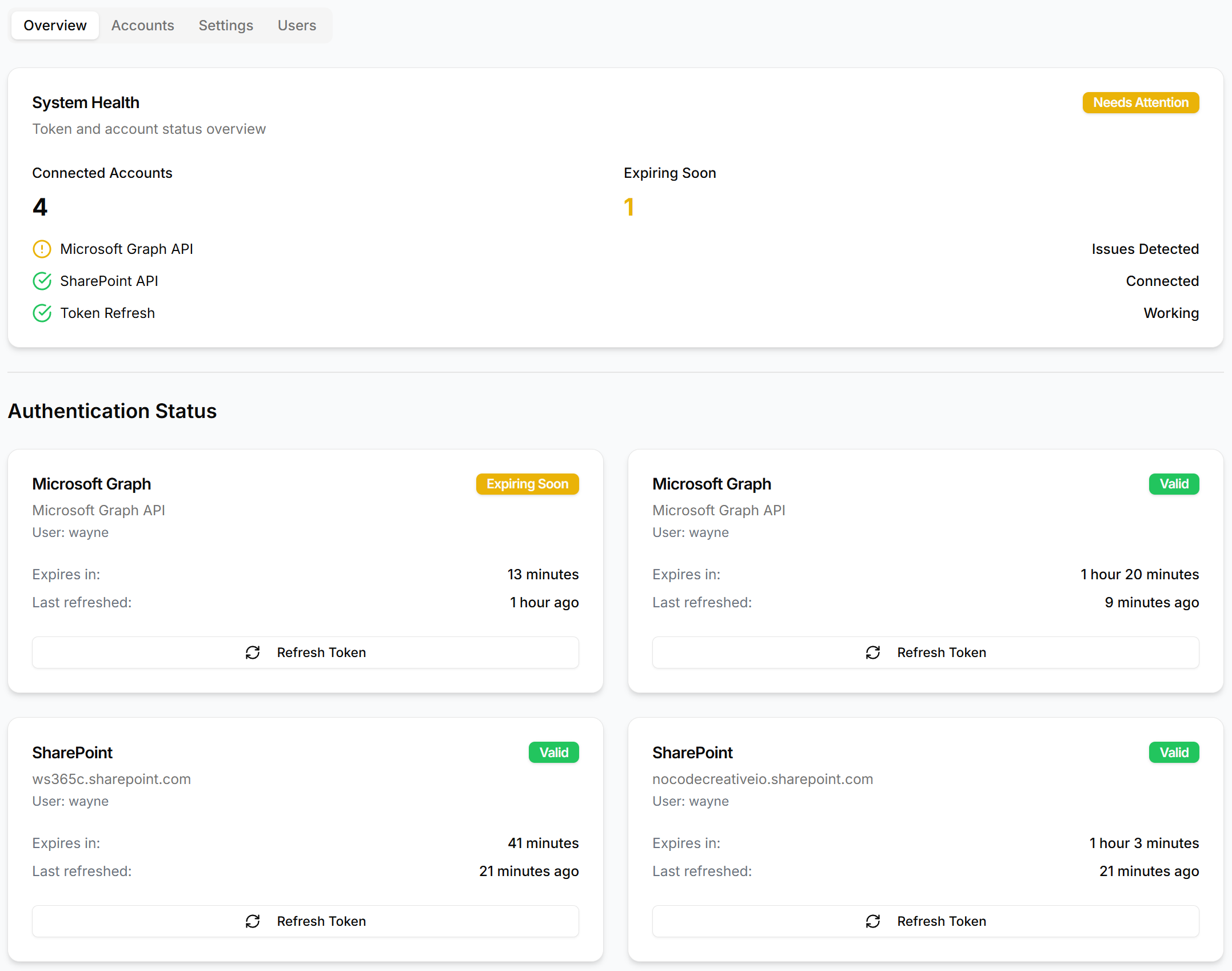
Perhaps the most sophisticated aspect is the automatic token refresh system. The system implements a comprehensive refresh mechanism that:
- Monitors token expiration with configurable buffer periods
- Automatically refreshes tokens using stored refresh tokens
- Updates token status in the database
- Handles refresh failures gracefully with appropriate error states
The cron job system in the system ensures tokens are refreshed every 45 minutes, preventing expiration-related failures.
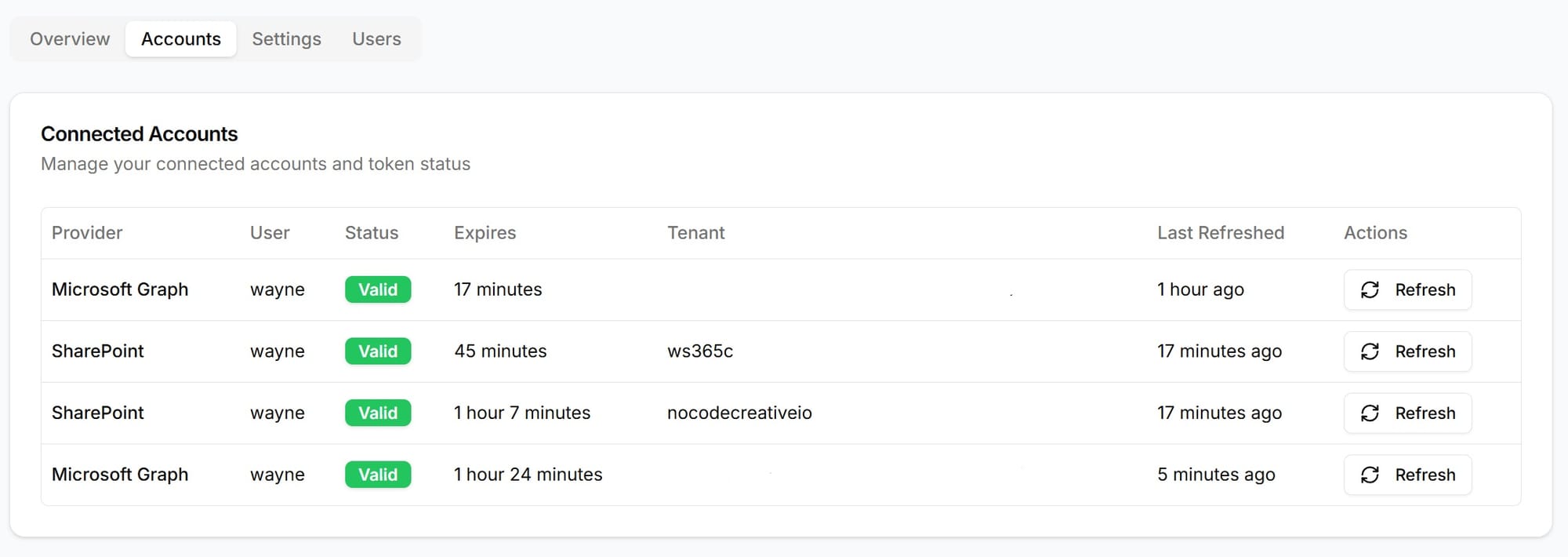
Multi-Tenant Support
The platform elegantly handles multiple SharePoint and Microsoft 365 tenants through a dynamic scope generation system.
Security Model
The security implementation is particularly impressive, employing multiple layers of protection across the entire stack.
Frontend Security
The Next.js frontend implements several robust security measures to ensure safe and reliable interaction with the platform:
- Microsoft OAuth Sign-In
Users authenticate via Microsoft’s secure OAuth 2.0 flow. This ensures that all login activity occurs through Microsoft’s identity platform, which provides built-in protections like multi-factor authentication (MFA), conditional access policies, and suspicious sign-in detection.
Upon successful login, a short-lived access token and refresh token are issued and securely stored by the backend. - Session Management via Secure Cookies
All authentication cookies are flagged asHttpOnly,Secure, andSameSite=Strict, and are transmitted exclusively over HTTPS. This ensures tokens are inaccessible to JavaScript, protected from interception, and bound to same-site requests only. - CSRF Protection
The frontend uses thecsrf-fetchutility to automatically handle CSRF tokens for all state-changing requests. This ensures that only requests originating from the app’s own UI are accepted by the backend, preventing malicious third-party request injection. - Input Validation
All user inputs on the frontend are validated before being sent to the backend using a strict schema-based approach. This prevents malformed or malicious payloads from reaching the server, enhancing both security and data integrity. - Domain Enforcement
The frontend only permits sign-ins from users associated with approved Microsoft tenants or email domains (e.g.@company.com), defined via theALLOWED_DOMAINSsetting and your Azure app registration. This ensures only authorised users from within your organisation can access the system.
Backend Security
The Express.js backend applies strong encryption and access control mechanisms to protect sensitive data throughout the authentication flow.
Token Encryption
Access and refresh tokens are never stored in plaintext. Instead, the platform uses AES-256-CBC encryption with best-practice safeguards:
- A cryptographic key is derived from a SHA-256 hash of the
TOKEN_KEYenvironment variable. - A random IV (initialisation vector) is generated for each encryption, ensuring unique ciphertext even for identical input.
- The IV and encrypted token are combined into a single binary buffer for easy and secure storage.
Tokens are only encrypted and stored — decryption is not performed by the backend. Instead, encrypted tokens are returned to authorised external platforms (e.g., n8n), which then decrypt them locally using the shared TOKEN_KEY. This ensures the backend remains stateless and avoids holding plaintext credentials in memory.
Authentication & API Security
- JWT Middleware: All internal API routes are protected by a JWT-based middleware that supports both header and cookie-based authentication.
- Role-Based Access Control: API access is governed by user roles (admin or user), ensuring that users can only access their own tokens while admins can query across accounts.
- Hashed API Keys: External API access is protected by SHA-256–hashed API keys stored securely in the database.
Database & Operational Security
- Sensitive fields such as encrypted tokens are securely stored using Prisma ORM with strict schema definitions.
- Environment variables are used for all secrets, with no hardcoded credentials in the codebase.
- The platform supports TLS connections for encrypted data-in-transit where applicable.
Authentication Middleware: The authenticateJWT provides robust JWT authentication with both header and cookie-based token support.
External API Security
The platform implements multiple security layers for external API access:
- API Key Authentication: SHA-256 hashed API keys stored securely
- Role-Based Access Control: API endpoints enforce user permissions based on roles
Deployment Guide (Docker)
The platform is designed for straightforward Docker deployment using the provided docker-compose.yml configuration.
Prerequisites
- Docker and Docker Compose installed
- Microsoft Azure application registration
Step-by-Step Deployment
1. Clone and Configure
git clone [repository-url provided on purchase]
cd microsoft-auth
cp .env.example .env
2. Configure Environment Variables
The .env.example file provides comprehensive configuration options. Key variables include:
# Application Environment
NODE_ENV=production
ENABLE_DEBUG_ROUTES=false
LOG_LEVEL=warn
# CSRF protection
ENABLE_CSRF=true
# Database Configuration
POSTGRES_USER=auth_user
POSTGRES_PASSWORD=auth_pass
POSTGRES_DB=auth_db
POSTGRES_PORT=5432
SERVER_PORT=3000
PRISMA_PORT=5555
POSTGRES_HOST=production-db-host
DATABASE_URL=postgres://${POSTGRES_USER}:${POSTGRES_PASSWORD}@${POSTGRES_HOST}:${POSTGRES_PORT}/${POSTGRES_DB}
# Security
TOKEN_KEY=generate-a-secure-64-byte-random-string
JWT_SECRET=generate-a-secure-jwt-secret
# Microsoft Azure AD
AZURE_CLIENT_ID=your-azure-client-id
AZURE_CLIENT_SECRET=your-azure-client-secret
AZURE_REDIRECT_URI=https://your-production-domain.com/api/oauth/microsoft/callback
# Microsoft Authentication Scopes
# Comma-separated list of scopes to request during Microsoft Graph authentication
MS_GRAPH_SCOPES=openid,offline_access,profile,email,User.Read,Mail.Read,Mail.Send,Calendars.Read,Chat.ReadWrite,ChatMessage.Send,OnlineMeetings.Read,OnlineMeetingTranscript.Read.All,Chat.ReadWrite.All,Files.Read.All,Sites.Read.All
# Comma-separated list of SharePoint scopes (without the tenant prefix)
MS_SHAREPOINT_SCOPES=AllSites.Read,MyFiles.Read,Sites.Search.All,Sites.Selected,User.Read.All
# Frontend Configuration
NEXT_PUBLIC_API_BASE_URL=https://your-api-domain.com/api
WEB_APP_URL=https://your-frontend-domain.com
COOKIE_DOMAIN=.your-domain.com
# Docker Configuration
COMPOSE_PROJECT_NAME=production-stack-name3. Azure Application Setup
Configure your Azure application registration with:
- Redirect URI:
https://your-domain.com/api/oauth/microsoft/callback - Required API Permissions: As defined in the MS_GRAPH_SCOPES and MS_SHAREPOINT_SCOPES variables
4. Deploy with Docker Compose
docker compose up -d --build
The docker-compose.yml configuration provides:
- PostgreSQL Database: Persistent storage with health checks
- Express.js Backend: API server with automatic migration handling
- Next.js Frontend: Web interface served on port 4000
- Networking: Internal Docker network for secure service communication
5. Initial Access
Access the platform at http://localhost:4000 (or your configured domain). The first user to authenticate will automatically receive administrator privileges.
Production Considerations
For production deployment, consider:
- Reverse Proxy: Use nginx or CloudFlare for SSL termination
- Database Backup: Implement automated PostgreSQL backups
- Monitoring: Add health check endpoints and logging
- Scaling: Deploy behind a load balancer for high availability
How to Access the Application
The MS Auto Auth 365 solution is available as a commercial solution with a unique access model designed for enterprise customers.
Acquisition Process
Pricing: The platform is available for an introductory price of £249, providing excellent value for enterprise-grade token management capabilities.
Purchase and Access:
- Upon purchase, you receive a unique product key via email
- The key grants access to the private GitHub repository containing the complete source code
- Repository access includes full documentation, deployment guides, and ongoing updates
- Access is tied to your verified GitHub account for security
Repository Access Benefits
Your product key provides:
- Full Source Code Access: Complete visibility into the platform's implementation
- Documentation and Guides: Comprehensive deployment and integration documentation
- Updates and Improvements: Ongoing access to platform enhancements
- Community Support: Issue tracking and community discussions
As stated in the LICENSE.md:
"Your validated product key grants you read-only access to the private GitHub repository containing the Software. This access includes full source code for review and customisation, documentation and deployment guides, updates and improvements during your license term."
Licence Summary
The platform operates under a comprehensive commercial licence that balances protection of intellectual property with practical business usage rights.
Permitted Uses
Internal Business Operations: Deploy and use the software within your organisation for internal automation workflows and Microsoft 365 integration.
Software as a Service (SaaS): Incorporate the platform into SaaS applications you develop, provided it remains integrated within your broader solution.
Consultancy Use: Development agencies and consultancies may deploy the software for client projects as part of custom solutions, with specific guidelines for source code access.
Key Restrictions
- No Redistribution: The software cannot be distributed, resold, or sublicensed as a standalone product
- No Source Code Distribution: Source code access is restricted to legitimate business purposes within your organisation
- Attribution Requirements: Public-facing applications must include appropriate attribution
Support and Compliance
The licence includes:
- Repository Updates: Access to software updates and improvements
- Community Support: Support through GitHub issues and the nocodecreative.io community discussions
- Validation Requirements: Product keys must remain active for continued access
Commercial Use Clarifications
The licence explicitly permits:
- Enterprise Deployment: Large-scale deployments across multiple departments and locations
- Revenue Generation: No restrictions on revenue from services incorporating the software
- Multi-Client Use: Consultancies may use a single licence for multiple client projects
As noted in the licence: "This License strikes a balance between protecting our intellectual property while enabling you to build sophisticated automation solutions that drive real business value."
Final Thoughts
The MS Auto Auth 365 solution represents a thoughtful solution to a genuine problem in the automation space.
For organisations struggling with Microsoft 365 automation complexity, this platform offers a path to centralised, secure token management that scales with your automation needs. The combination of enterprise-grade security, comprehensive API access, and straightforward deployment makes it a compelling solution for teams serious about automation infrastructure.
The £249 price point, coupled with full source code access and ongoing updates, provides excellent value for what could otherwise require significant internal development resources to achieve the same level of security and reliability











